Understanding Token Approvals: Benefits, Risks and Best Practices
Understanding token approvals is essential for anyone in crypto. Learn more about the benefits, risks, and best practices for approvals so your funds can stay safe.

In the flourishing world of Web3, the digital landscape is undergoing a seismic shift. Decentralized systems and applications are at the forefront of this transformation, promising to remove intermediaries and to ensure transparency and user empowerment. One of the important mechanisms enabling this decentralized revolution is token approvals. These approvals ensure that while you enjoy the benefits of decentralized platforms, your assets remain secure and under your control. In this article, we will look into the benefits, risks, and best practices regarding approvals.
Key takeaways
- Definition of token approvals: Token approvals, also known as token allowances, are permissions granted by token holders, allowing specific contracts to access a set amount of their tokens.
- Evolution of approvals: From the traditional approve() function to innovations like EIP2612 and Permit2, token approval mechanisms have evolved to enhance user experience and security.
- Risks and scams: Token approvals can be targeted by bad actors, making it essential to understand permissions and be cautious with unknown or untrusted contracts.
- Best practices: Make sure to regularly monitor and manage token approvals using tools like Revoke.Cash. Always verify the legitimacy of contracts or dApps before granting permissions.
What are token approvals?
Token approvals, or token allowances, refer to the permissions granted by token holders. This permission allows specific smart contracts to access and operate with a predetermined amount of their tokens. For instance, if you've ever used a decentralized exchange or interacted with a DeFi protocol, you've likely encountered a prompt asking you to approve the platform to access your tokens. This is token approval in action. It's a foundational aspect of many decentralized applications, enabling functionalities we often take for granted. For example, when you list an NFT for sale on a platform like OpenSea, you essentially give the platform approval to transfer the NFT on your behalf once a buyer is found.
Why do we need token approvals?
Blockchain's essence is about returning power to the individual. In this decentralized paradigm, you, the user, should have full sovereignty over your assets. No entity, decentralized or otherwise, can access or manipulate your assets without your explicit permission. Token approvals are the embodiment of this principle in action.
Consider the workings of Decentralized Exchanges (DEXs) like Uniswap. If you wish to swap Ethereum (ETH) for USDC, you first need to give Uniswap the green light to access your ETH. This approval ensures that Uniswap can facilitate the swap on your behalf, making the process seamless.
Similarly, on Lending Platforms like Aave, if you want to earn interest on your tokens, you first approve the platform to access and lock your tokens in a lending pool. This ensures your tokens are safely staked, and you earn the promised interest.
NFT Marketplaces like OpenSea also rely on token approvals. Before listing your prized NFT for sale, you grant the marketplace permission to handle the NFT's transfer once it's sold. This ensures a smooth sale process without needing you to be online and approve the sale when a buyer is found.
Lastly, Staking Protocols such as those on Eth2.0 or other Proof-of-Stake chains require token approvals. Before you can stake your tokens and earn staking rewards, you give the staking contract permission to lock up your tokens, ensuring they're correctly staked and you receive your due rewards.
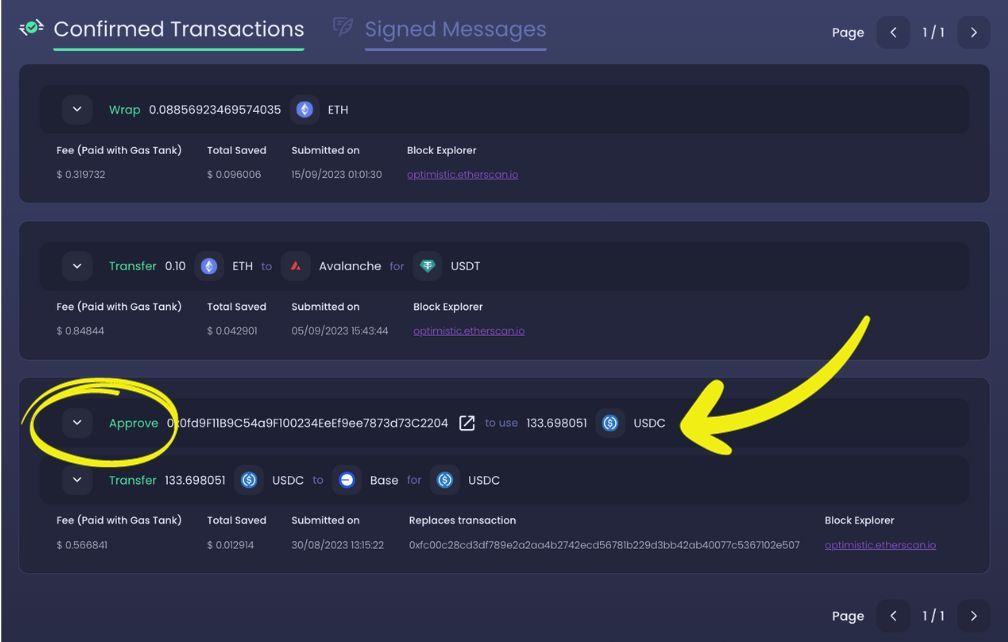
The evolution of token approval mechanisms
As the decentralized ecosystem has matured, so too have the mechanisms that underpin its operations. Token approvals, central to many Web3 interactions, have seen significant evolution in their design and implementation. From the early days of the traditional approve() function to the recent innovations like EIP-2612 and Permit2, the journey reflects a continuous effort to enhance user experience, reduce costs, and bolster security. Let's delve into this evolution, understanding each mechanism's nuances and the strides made in improving upon previous versions.
Traditional token approval mechanism
The traditional approve() function, as defined in the ERC20 token standard, has been the foundation of token approvals since the inception of Ethereum-based tokens. This mechanism requires you to approve a certain amount of tokens for a contract before the contract can transfer those tokens on your behalf. While this method certainly still works, it has several drawbacks:
- Gas Fees: Every approval is an action on the blockchain, which means it requires a separate transaction - and this leads to additional gas fees. If you want to interact with multiple contracts or perform multiple operations, the costs can add up.
- Repeated Authorizations: If you exhaust your approved amount for a particular contract, you must approve again, leading to redundancy and a less-than-ideal user experience.
- Security Concerns: Unlimited approvals can pose risks (e.g., approving a dApp to interact with all your tokens in a specific currency). If a malicious actor gains control of a contract with unlimited approval granted, they could drain your tokens.
EIP-2612 Permit signatures
EIP-2612 introduced a novel approach to token approvals called Permit signatures. This mechanism allows you to sign a message off-chain, granting permission to a contract. The contract can then use this signature to verify and execute the approval on-chain. The benefits of this method include:
- Gasless Approvals: Since the approval is signed off-chain, you don't need to spend gas until the actual on-chain transaction occurs.
- Improved User Experience: You can grant approvals without making a separate blockchain transaction, streamlining interactions with dApps.
- Enhanced Security: EIP-2612 reduces the risks associated with unlimited approvals by allowing you to set precise limits and expiration times for your approvals.
However, EIP-2612 is sadly not universally adopted and still requires tokens to integrate this standard, even though it would be a significant improvement.
Permit2
Developed by the Uniswap team, Permit2 is the next evolution in token approval mechanisms. It builds on the foundation laid by EIP-2612 but aims to make gasless approvals universal for every token. Key features and improvements of Permit2 include:
- Universal Gasless Approvals: Permit2 is designed to work with any token, regardless of whether it has integrated EIP2612 or not. This broadens the scope of gasless approvals, making them accessible to a wider range of tokens and users.
- Automatic Expiration: One of the standout features of Permit2 is the automatic expiration of approvals. This adds an extra layer of security, ensuring that lingering approvals don't pose a risk in the long run.
- Reduced Complexity for Developers: Permit2 simplifies the approval process from a developer's perspective, making it easier to integrate and use in various dApps and protocols.
By addressing the limitations of the traditional approve() function and EIP-2612, Permit2 presents a forward-looking solution that balances user experience, security, and developer convenience.
The importance of revoking token approvals
Token approvals, while a powerful tool in the decentralized ecosystem, come with their own set of challenges and risks. At the heart of these risks is the very nature of token approvals: they grant permissions to external entities to interact with your tokens. While this is essential for many Web3 functionalities, it also opens the door for potential misuse, especially by bad actors.
How token approvals could enable scams?
One of the darker sides of token approvals is their potential use in scams. Bad actors can create malicious contracts or dApps that, once approved, drain tokens from unsuspecting users. For instance, a scam dApp might ask users for token approvals under the disguise of a legitimate service, only to exploit this approval to siphon away tokens.
The risks associated with token approvals are multifaceted. One of the primary concerns is the granting of unlimited approvals. If a user unknowingly grants unlimited access to their tokens, a compromised or malicious contract can drain their entire balance. Furthermore, lingering approvals, especially those with high or no set limits, can be a ticking time bomb. Even if a user no longer interacts with a particular dApp or contract, an existing approval can still be exploited.
Permission and exercising caution
It's paramount for all users to understand the permissions they grant when approving tokens. Every approval should be seen through the lens of trust: Do you trust the contract or dApp with access to your tokens? If there's any doubt, it's better to err on the side of caution. This is especially true when interacting with unknown or unverified contracts. Always verify the legitimacy of a contract or dApp before granting any approvals.
Best practices for token approvals
Token approvals are a crucial mechanism in the decentralized world, allowing you to interact seamlessly with various dApps and protocols. However, with the power of token approvals comes the responsibility of using them wisely. Here are some best practices to ensure the secure and efficient use of token approvals:
Limit and monitor your approvals
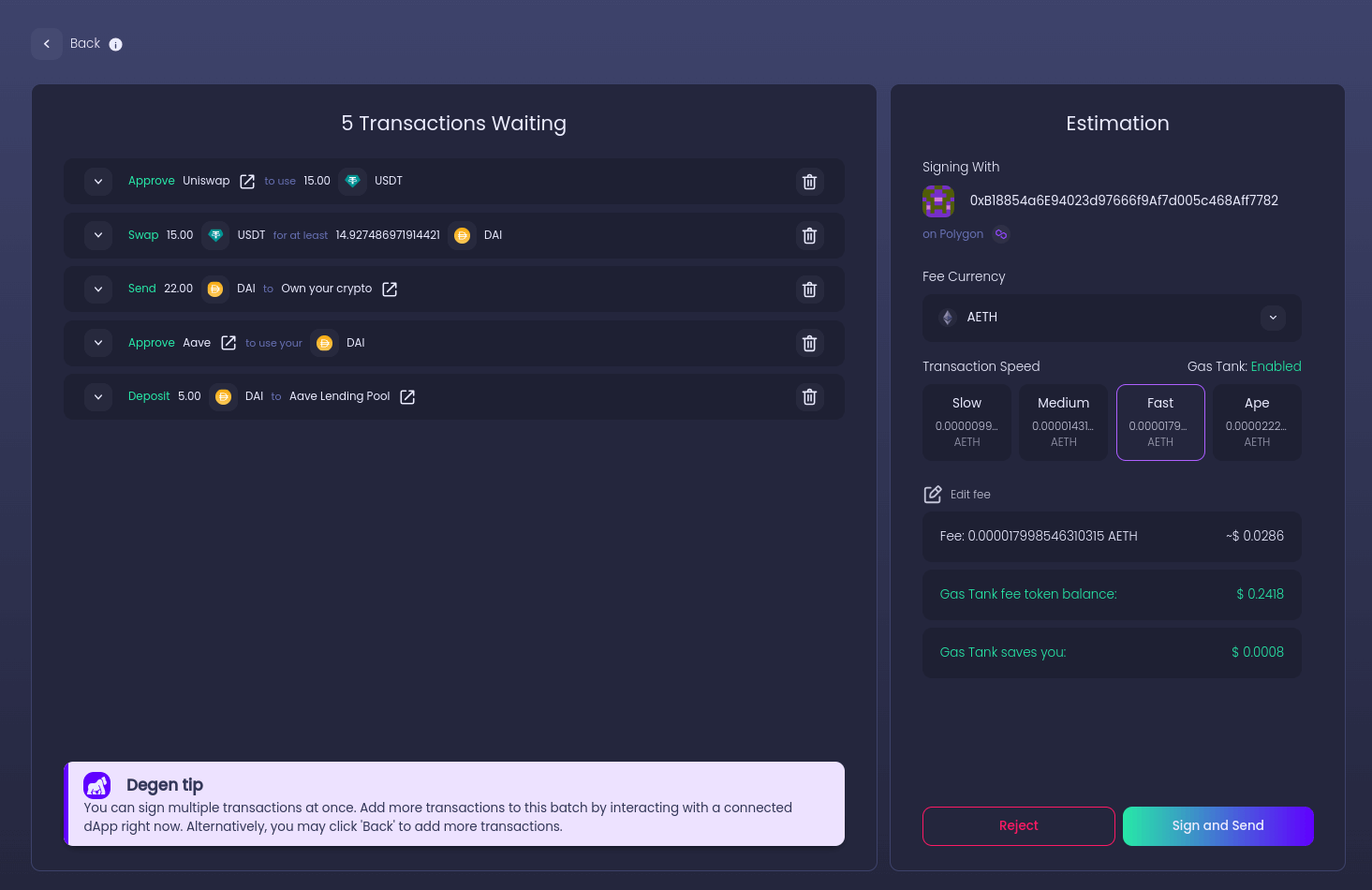
It's essential only to approve the amount of tokens you intend to use. Granting unlimited approvals can be a potential security risk, especially if the contract or dApp becomes compromised. Smart contract wallets, like Ambire Wallet, have introduced mechanisms that batch the approval with the actual transaction, ensuring that users only grant limited approvals. This not only reduces the exposure of the full asset amount but also mitigates risks associated with upgradable smart contracts. Additionally, users should regularly monitor and manage their token approvals, revoking any that are no longer necessary or seem suspicious.
Ambire Wallet has a further feature called transaction simulation. This simulation allows you to preview the outcome of your transactions before signing, ensuring accuracy and reducing the likelihood of errors. This essentially means you can see what your balance will be after you sign your pending transactions - and reject transactions that look suspicious if the balance isn’t what it should be.
Understand the risks and potential for scams
Token approvals can be a double-edged sword. While they enable seamless interactions with dApps, they can also be exploited by bad actors. Scammers can create malicious contracts or dApps that, once granted approval, can drain tokens from unsuspecting users. It's crucial to be cautious and understand the permissions you're granting. Always verify the legitimacy of a contract or dApp before granting any approvals, and be wary of unknown or untrusted contracts.
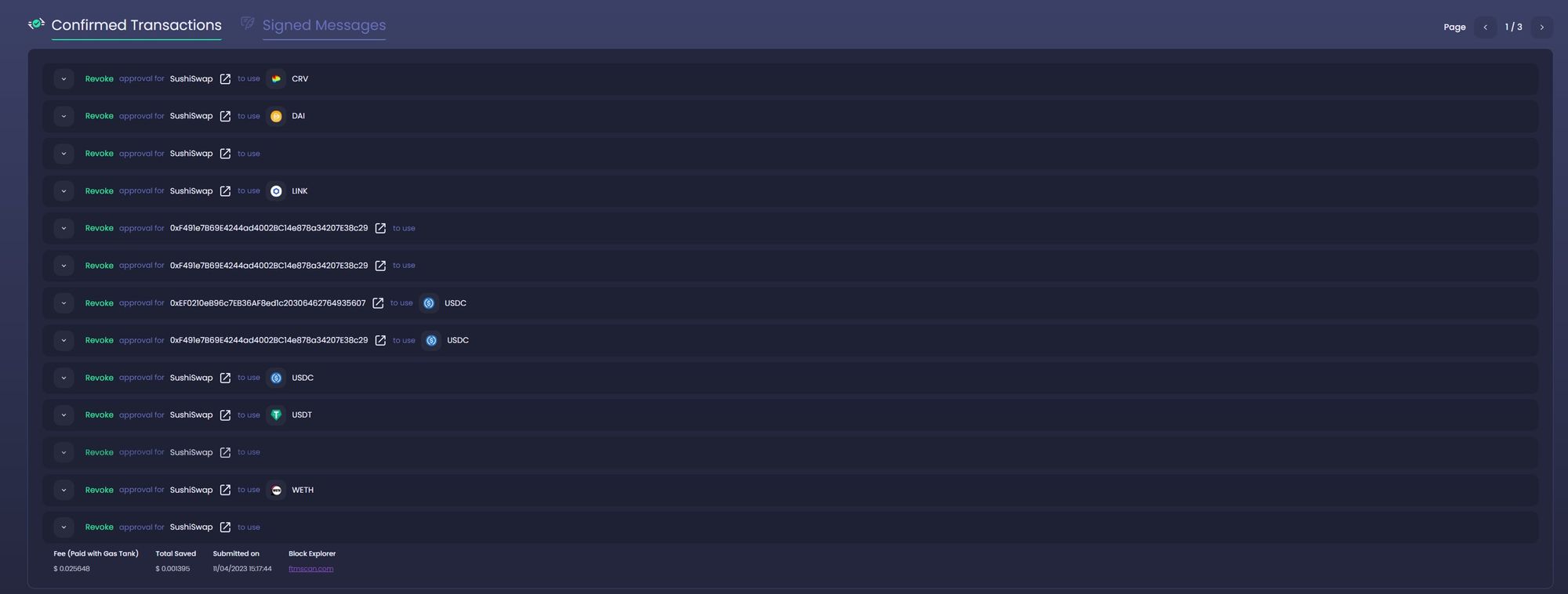
Utilize tools to manage and revoke approvals
Several tools have been developed to help users manage and revoke token approvals across various networks:
- Revoke.cash: This is the most popular tool for revoking token approvals. It supports over 60+ different networks and works with all major wallets. Users can easily search for their approvals and revoke them as needed. Etherscan and Other Explorers: Platforms like Etherscan, Polygonscan, Arbiscan, Fantom, Optimistic Explorer, and BscScan allow users to view and revoke token approvals. While they might not be as user-friendly as dedicated tools like Revoke.cash, they are reliable and widely used in the crypto community.
By understanding and implementing these best practices, users can ensure a safer and more efficient interaction with dApps and the broader Ethereum ecosystem.
Conclusion
Token approvals stand as a testament to the innovative nature of the decentralized ecosystem, enabling seamless interactions between users and dApps. As we've explored, while they offer numerous benefits, they also come with their own set of challenges and potential risks. From understanding the evolution of token approval mechanisms to recognizing the importance of revoking unnecessary approvals, it's clear that user awareness and proactive management are paramount.
The emergence of tools and platforms, such as Revoke.cash and Ambire Wallet, further underscores the crypto community's commitment to enhancing security and user experience. By staying informed, regularly managing approvals, and leveraging the right tools, users can navigate the Web3 landscape confidently while safeguarding their assets.
In this ever-evolving space, it's essential to remain vigilant, continuously educate oneself, and adopt best practices. As the decentralized world continues to grow, so too will the mechanisms and tools that support it, ensuring a safer and more efficient future for all.
Related articles
Transaction Batching 101, or How to Streamline Crypto Transactions
Interested in Ambire? Follow us:
Discord | X (Twitter) | Reddit | GitHub | Telegram | Facebook
