How to Stay Safe Online: Your Personal Cyber Security Guide
Learn how to protect your digital assets with this comprehensive guide covering passwords, email security, and other best practices.

Best practices for staying protected on the internet
We’ve written about protecting your crypto assets before - you can check our crypto opsec guide here. Now it’s time to prepare a set of more general tips to help you stay safe online - we know you’re probably doing most of your shopping online and we really don’t want you to get hacked.
Remember: you can never be too secure when you’re exploring the internet, and these little tips will help you stay protected.
1. Take good care of your passwords
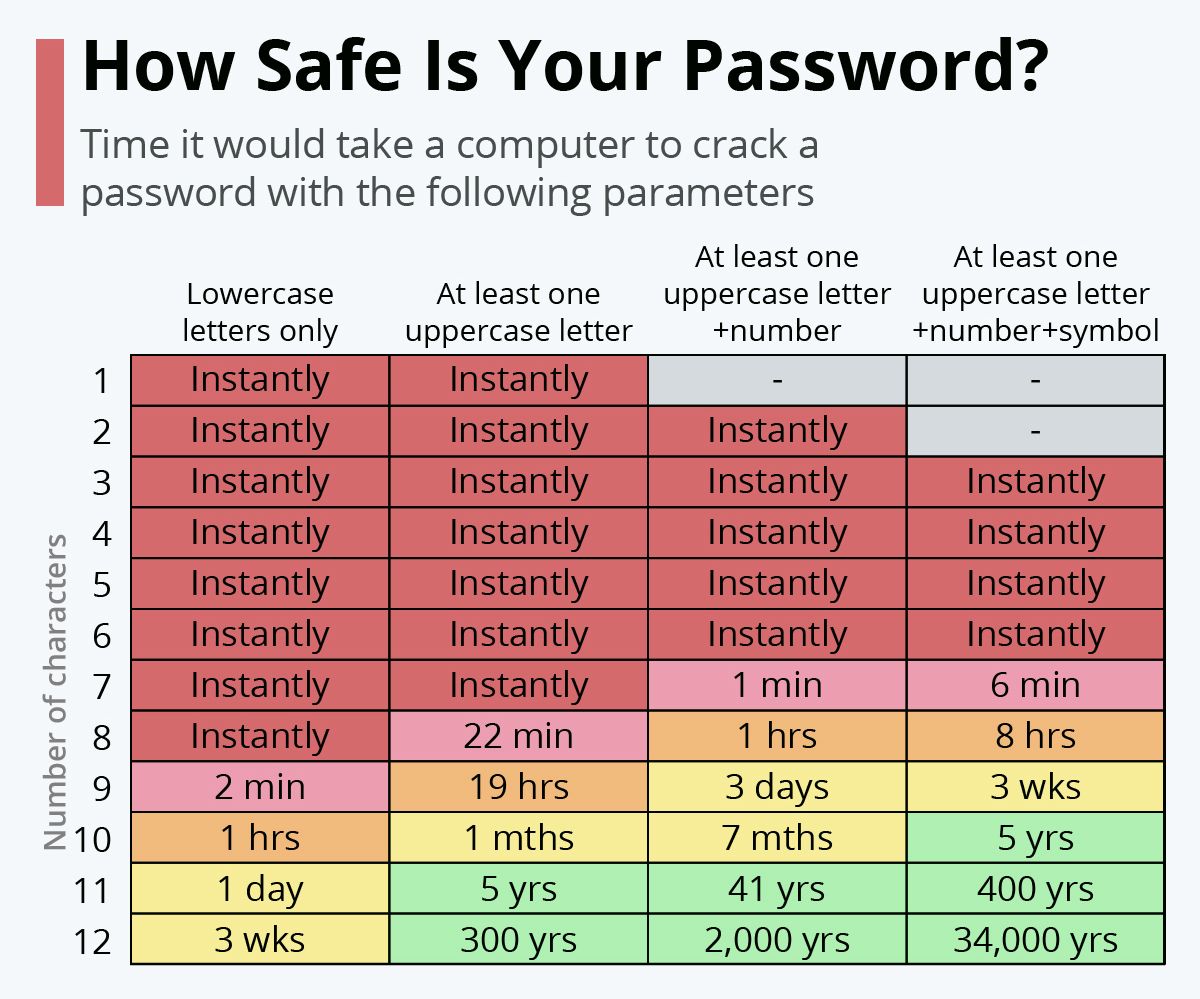
Choose long and secure passwords
We all know how important it is to choose secure passwords - yet way too many people still put their kids’ names, birthdays, 123456 or other easy to guess passwords for their online accounts. We get it - you have enough on your mind, and coming up with a complex passphrase takes mental effort but you can do better than “password” for a password.
Keep in mind that the longer your password is, the better - and adding special characters makes it even harder to hack your passphrase.
Don’t reuse passwords
Using the same password for multiple online accounts is another thing people are tempted to do. You already thought of one super long and complex password for your email, so it makes sense to reuse it for other accounts, right? Wrong!
Passwords get leaked. They are being sold online. Did you know that you can acquire a database of peoples’ login credentials faster and cheaper than you can get a latte at Starbucks? You can, we checked.
Don’t compromise your online security by using the same password twice.
Change passwords regularly
Changing your passwords is a hassle but so is washing your clothes for example. Yet you wear a fresh pair of socks every day; so why shouldn’t you practice good online hygiene too?
Make sure that the passwords you use most often are changed on a regular basis. The same goes for accounts that have your payment details and other sensitive information saved.
Use a vetted password manager
Remembering all of your passwords is hard. Hell, remembering what you had for breakfast is hard, let alone remembering a larger number of random character sequences.
It’s ok to use a password manager. Our recommendation is to select a password manager that is open-source, audited and reputable. Мake sure to do thorough research when choosing a password manager!
2. Regularly check if your email has been leaked
Make it a habit to check if your email address has been leaked. Sites like Have I been pwned (free), mypwd (free) and Dehashed (paid) can show you if your details have been exposed in hacks/data leaks.
If your email appears on any of these databases, change your password immediately! Also make sure to check for your current active login sessions and end any session that you don’t recognize.
3. Keep separate email accounts
This is not a piece of advice that you’ll see often, however we find it to be a best practice when it comes to cybersecurity.
We recommend that you keep a separate email account for signing up for products and services - not the email account that you use for, well, emailing.
Even better if you separate your emails into different “levels” - here’s what we mean:
- Have one email address for super important accounts - your online banking, your crypto wallet, etc. - do not share this email address with anyone!
- Have another account for accounts that you use often but don’t contain sensitive data like credit cards etc. These could be your social media accounts for example.
- A separate email account for your online shopping.
- An email account that you use to email people and exchange messages.
This way if one of your email accounts gets compromised, you can limit the potential damage.
4. Use two-factor authentication (2FA)
The year is 2022. Two-factor authentication is an absolute must for every account where you can enable it and even your grandma uses it.
We recommend that you use a device app like Google Authenticator or Authy when possible, and not an SMS 2FA - text messages are super easy to intercept so the SMS option is the less secure one.
If you have a second device where you can back up your authenticator app - do it!
5. Set a password for all your hardware devices
Make sure that all of your devices - computers, phones, tablets - are password-protected, even if they’re only for personal use. Having a password means that if your device gets lost or stolen, your data is protected and cannot be accessed by unauthorized people.
If possible, also encrypt your device discs.
6. Don’t leave your devices unlocked
If you’re leaving your devices unattended, make sure that they’re locked - even if you’re only letting them out of your sight for a very short while.
Going to the bathroom at a cafe and leaving your phone on the table? Lock it. Entertaining guests at your home and your computer is in the room? Lock it. Think of your devices as of the homes of your data - and we lock our homes when we leave.
7. Use temporary credit cards when possible
If you’re online shopping, use a temporary credit or debit card whenever possible. This is especially important if you’re buying something from a site that you’re not familiar with and you haven’t researched well.
Make sure that you don’t use temporary cards for recurring payments though - these cards are “burnt” after being used and they won’t be active for subsequent purchases.
If you’re not sure how you can use such a card, ask your bank - many banks offer that as a service for a tiny fee. You can also use fintech apps like Revolut where you can generate temporary cards as well.
8. Use a VPN
Using a VPN service means that you’ll make it harder for hackers, internet service providers and other companies to snoop on your online activities. And even if you’re ok with your ISP tracking all the weird stuff you do on the internet, still use a VPN.
VPNs do not only help to protect your privacy online, but also improve your online security, as they encrypt your internet connection and can protect you from hackers and other cybercriminals.
9. Don’t download random apps
If you see an ad that promises to make your phone twice as fast, it’s a bad idea to click on it and install an app. It will not make your phone faster. What it will do is inject malware into your phone or at the very best - show you a million ads per hour (honestly, we don’t know which is worse).
Overall, be extremely careful about the apps you download. Check if they are published by a reputable developer; search for words like “scam” and “malware” in the reviews; make sure you are downloading from an official app store/site.
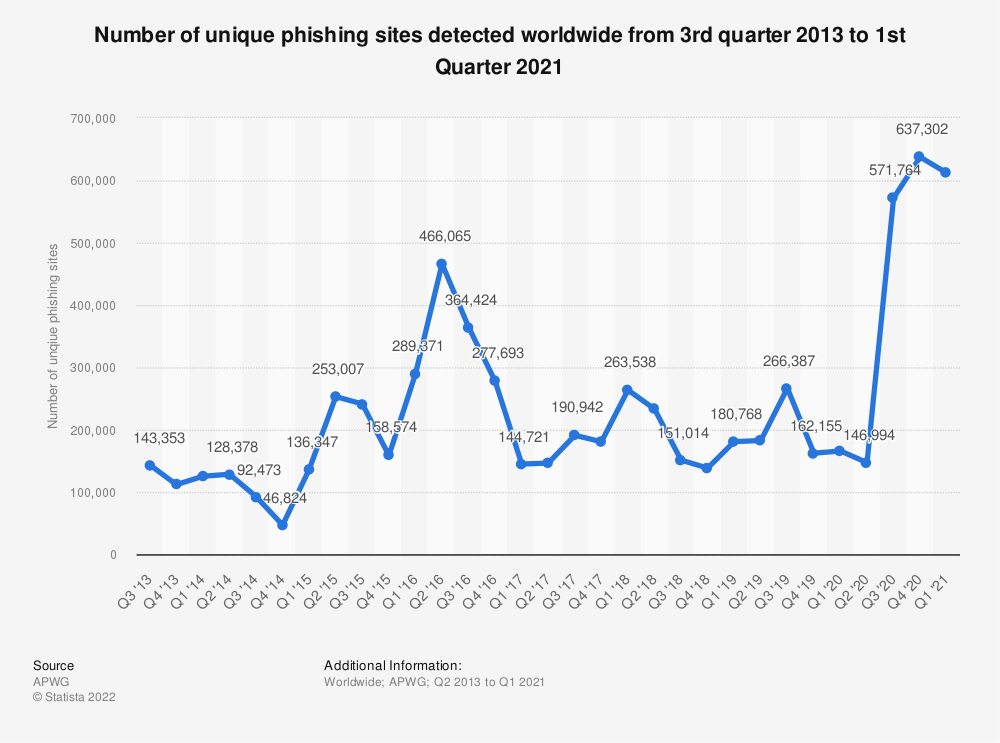
10. Beware of phishing scams
Phishing is the most common type of cybercrime. Hackers are able to mimic a legitimate website or an official email to the point of it being unrecognizable from the original one. To protect yourself from phishing, always double check the URL before logging in, providing personal data or entering payment information.
If you get an email from Amazon, for example, and it asks you to update your payment information, don’t click on the links in the email. Instead, go straight to your Amazon account and look for notifications about that.
Or if you click on a link/button in your email, make sure it leads to a legitimate website and not to www.definitely-not-trying-to-steal-your-credit-card-info.com or another sketchy URL.
If you get a text message from your bank and it has a link to log in, again - don’t click on the link but go to your online banking portal instead and check if your account is in good standing there.
11. Limit browser extensions use
Browser extensions are notoriously easy to spoof and hack, so use as few of these as possible. Just as with apps, it is important to make sure you check who is the browser add-on developer, what permissions does the extension have, and whether you are in fact downloading the original extension and not a phishing/malware version that looks identical to the real thing.
12. Install software updates on time
Pay attention to all software updates that are available for your devices - laptop, phone, tablet, etc. We know you have more important stuff to do but these often contain security vulnerability patches that protect you from known security exploits. Just muster the courage to click on that “Install updates” button, we know you can do it!
13. Avoid unsecured Wi-Fi networks
Don’t connect to random Wi-Fi networks unless you absolutely have to. Doing so opens your device to anyone else on that same network, and you don’t know who else is there and how well-intentioned or malicious they are.
Public cafe networks, the Wi-Fi at the airport, hotel networks without passwords, etc. are better left alone.
14. Be careful about the information you put online
Frankly, the only person who’s genuinely interested in when and where you’re going on vacation, where you shop online, or what your Christmas tree looks like this year is your ex. And hackers who can potentially benefit from that information.
We don’t often realize that but we put a lot of information about ourselves online - and this information could be easily used against us.
Before you post a picture of yourself with a location, or an image of your password and boarding pass - think twice. Who can use this information? How can they use it? Where are you vulnerable? Don’t forget that data can be pieced together so things that seem harmless on their own can easily become a part of a social engineering hack, identity theft or another cyber attack.
15. Backup your data
Regular backups of your important files and documents ensure that you won’t lose anything in the case of a ransomware attack. Ideally you should be maintaining multiple up-to-date backups of your data - and it’s good if at least one of them is on a cold-storage device like an external hard drive for example.
Why should you care about your online safety
The estimated cost of cybercrime is 8.44 trillion US dollars globally for 2022 alone - expected to get to 23.84 trillion in 2027. If that alone is not a reason for you to care, we don’t know what is.
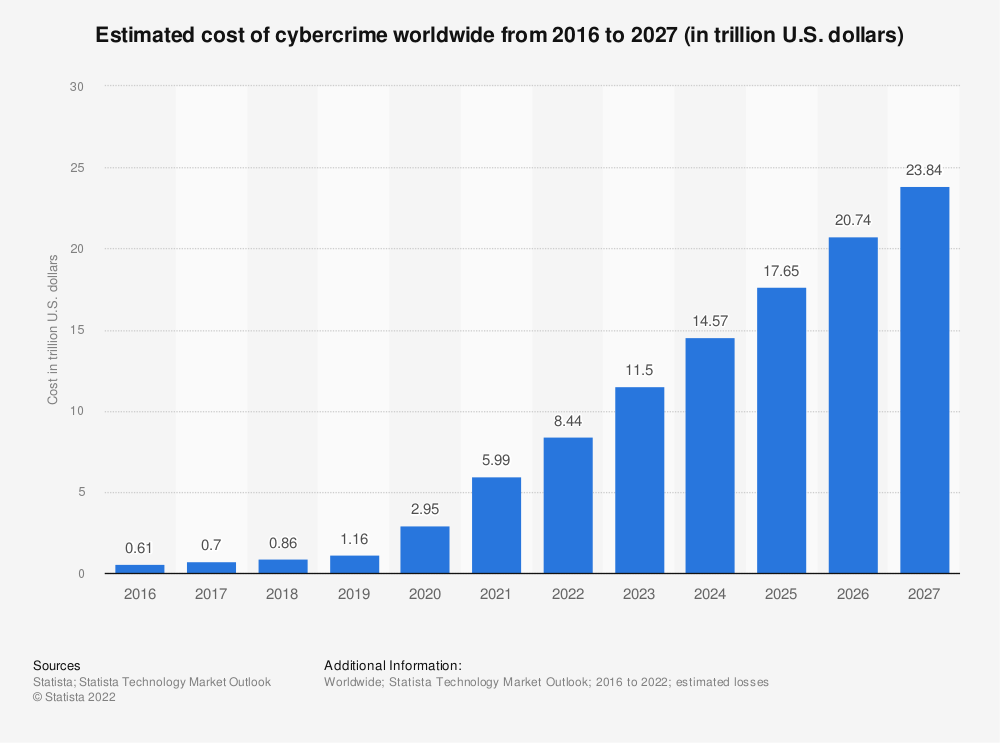
Out of these, phishing is the most common culprit, closely followed by personal data breaches and identity theft. All things that can be easily prevented if we’re extra careful with our data, payment information and practice internet safety.
Interested in Ambire? Follow us:
Discord | X (Twitter) | Reddit | GitHub | Telegram | Facebook
